DDos Attack Map
D-Dos attacks on computer systems are made to develop conditions in which a user has obstacles to the collection of necessary data and the access to necessary resources and services. Regardless of the type and quality of the server equipment, whether this be HP ProLiant XL220a Gen8 v2 or Lenovo Flex System x440, a distributed attack made from several PCs at once can easily cause service denial of even highly protected resources.
Where do they come from and how to deal with them?
Such attacks are usually performed with the help of computers previously infected with virusware, called “zombies”.
There are several reasons why your server can be subject to the DDoS attack:
1 Fraud. If the protection is not reliable enough, hackers can cause complete denial of a system with the intention of demanding a certain amount of money to unblock a resource.
2 Rivalry/competition. A firm competing with another one asks a hacker to attack the system partially or completely or to paralyze the rival company’s internal and external resources.
3 Vandalism – these are attempts of newbies to test their skills or to simply entertain themselves.
The primary and the most effective way to fight the abovementioned inconveniences is to create distribution systems. They allow serving users even in case some cross points crash. Aside from using various network and server hardware, it is even better to vary their physical location when building distribution systems. Besides, the installation of fail-safe clusters in other countries can ensure the security of your information not only from DDoS attacks, but also from destructive incidents in data centers or global disasters capable of damaging the equipment.
It is also a good practice to install the monitoring and notification system recognizing the attributes of a DDoS attack, which will help react to a threat in time and take necessary actions.
DDos Attack Map:
MAP.NORSECORP.COM – Norse Attack Map.
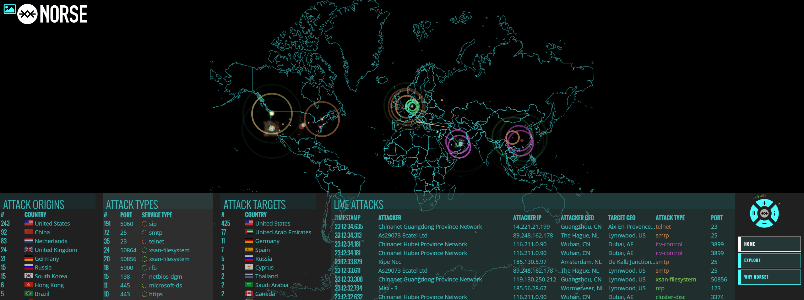
MAP.NORSECORP.COM
DIGITALATTACKMAP.COM – Digital Attack Map. Digital Attack Map – DDoS attacks around the globe.
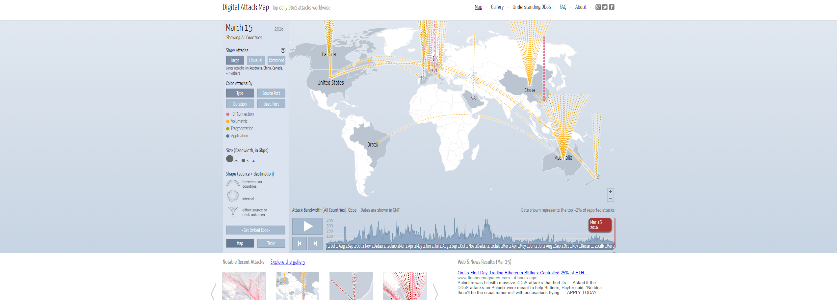
DIGITALATTACKMAP.COM
CYBERMAP.KASPERSKY.COM – Kaspersky Cyberthreat real-time map.
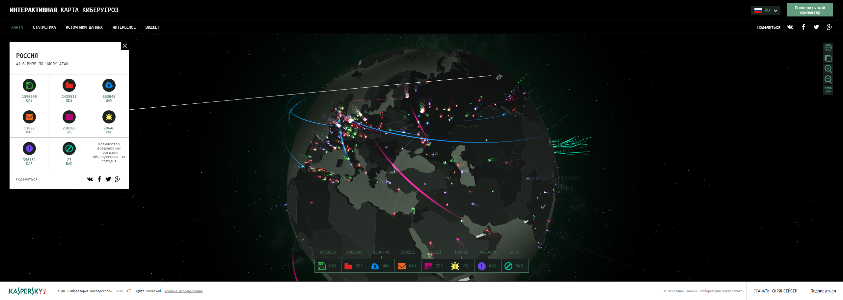
CYBERMAP.KASPERSKY.COM
FIREEYE.COM – The “FireEye Cyber Threat Map” is based on a subset of real attack data, which is optimized for better visual presentation.
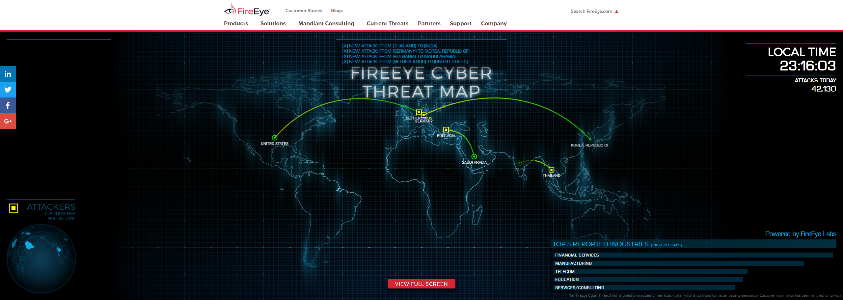
FIREEYE.COM
Personal contact info – slikgepotenuz@gmail.com
Permanent Address :- Montville, NJ
CEO and co-founder at Cloudsmallbusinessservice.com